How to detect malicious packets if they are encrypted?
How do we protect against malware if we can’t even read the packets containing the malware?!

How do we protect against malware if we can’t even read the packets containing the malware?!
Should we decrypt traffic for inspection?!. This can be very processor-intensive (thus very expensive), and the decryption of traffic might violate companies’ security policies.
One of the ways t solve this problem is by using what is called Encrypted Traffic Analysis (ETA). ETA can check encrypted traffic for offending payloads. This technology is used by Cisco, integrated into its latest devices.
ETA looks for symptoms of malware in encrypted traffic. Using huge data sets, Cisco has been able to determine the characteristics of encrypted traffic carrying both benign and infected packets.
The ClientHello Message: At the beginning of a TLS session, a client sends a ClientHello message. This initial packet is not encrypted, because it contains information used to negotiate the encryption. For example, the ClientHello message contains a listing of cipher suites that it supports, and which cipher suites it prefers to use. A cipher suite contains parameters used to negotiate the formation of an encrypted TLS connection. Examples of these parameters are: the type of authentication used, the type of encryption used, and the algorithms used to exchange keys. The list of cypher suites varies widely based on the type of client (e.g. desktop vs. mobile) and type of application. This means if suspicious cypher suite listings (which have been learned to accompany malicious traffic) are detected, the traffic can be blocked.
Packet Lengths and Times: Cisco again turns to its huge data set to learn the lengths of packets for specific connection types and time intervals between packets required to complete specific requests. If the packets making a request in an encrypted TLS connection have a statistically significant variation from known packet length and time values for benign traffic making similar requests, ETA can conclude the traffic probably contains malware.

Here is a good article that explains it in more details Detecting Encrypted Malware Traffic (Without Decryption)
TLS Inspection and SSL/TLS Accelerator
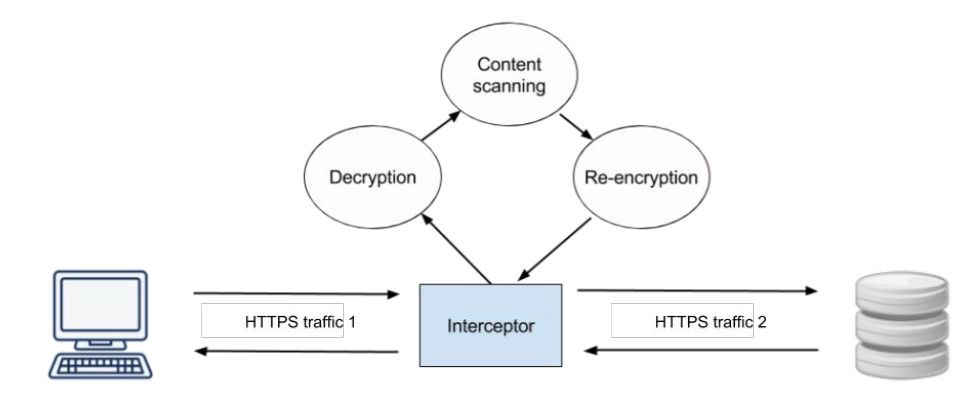
TLS inspection is computationally demanding, may violate privacy policy, and expensive.
A computer or an add-on card. Some organizations have a policy that states that SSL/TLS encrypted data needs to be decrypted when it reaches the internal network and then analyzed for malware and potential attacks. It is often then re-encrypted and sent to its final destination. This can be done using an SSL/TLS Accelerator.